1. Medical records fetch a high price on the Dark Web.
2. Criminals know that attacks against hospitals work.
In the past year, stories of hospitals being taken offline by ransomware and other malware have become regular fixtures in the headlines. From an infection that forced MedStar Health to shut down computers at 10 hospitals and more than 250 outpatient centers last March to an attack on Texas-based Rainbow Children’s Clinic that affected 33,638 patients in August — in each of these cases, hospital administration and staff have been left scrambling to determine not only how the security they had in place was breached, but how best to recover while keeping critical, life-saving services up and running.
More often than not, the answer to the former question is discouragingly simple. Take, for example, the recent malware infection that forced parts of Barts Health NHS Trust, the UK’s largest hospital group, offline in January. After investigating the attack, Barts NHS deputy chief executive Tim Peachey lamented that, “the trust’s antivirus software had been up to date,” but it had been bypassed because the malware involved was “a new virus not seen previously.”
With existing protections that can be bypassed when malware is new or disguised, hospitals have been forced to turn their hopes away from preventing attacks and focus instead on detecting and recovering from them. That often boils down to taking systems offline, wiping them, and restoring everything from backup. While that may theoretically be a feasible for a small businesses, we’ve seen what it can look like for hospitals that can ill afford downtime.
Last February, Hollywood Presbyterian Medical Center was forced to shut down its systems for 10 days in response to a ransomware attack, resulting in a critical loss of access to patient data, large-scale disruption to a wide variety of services, and an internally-declared state of emergency. The loss in revenue from the disruption to CT scans alone was estimated at $1 million. The attack on Barts Health was comparably well contained, yet still resulted in multiple systems, including pathology, being taken offline for multiple days.
Hospitals excel at identifying the root causes and best treatments for illnesses, and they are seldom satisfied with simply addressing the symptoms of an underlying problem. In the case of these ransomware attacks, there is a real parallel. Malicious software is mutating quickly, creating blind spots for existing protections. In order to prevent the damage — the “symptoms” of these attacks — there is a need for a new layer of security that will diagnose malicious behaviors, even if the particular “illness” hasn’t been seen before.
This new layer needs to kick in when malicious code works its way past file-scanning solutions, but before it corrupts the system and causes damage that becomes visible to detection tools. In other words, this protection has to defend the system from malware at runtime.
Hospitals protection needs to include runtime malware defense
Security has traditionally protected hospitals by addressing their concerns before and after malicious software has attacked their systems.
There are groups of tools that prevent recognized attacks from being initiated, and when attacks get through, there are other tools designed to detect and recover from the damage.
Looking at the malware lifecycle, however, we see that there is a third stage in between those two points. By shifting some of their focus to blocking malware during runtime, hospitals gain the additional ability to stop attacks after execution has been initiated, but before any damage is done.
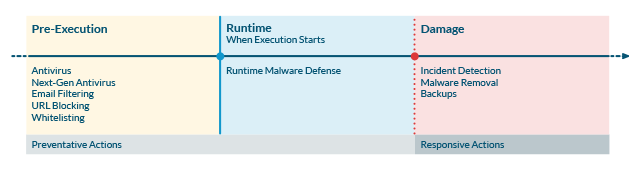
Hospitals need to map their security to all three stages of the malware lifecycle
Maximizing Protection Across Malware Stages
In order to protect hospitals from the types of attacks that are dogging them, security managers and IT pros need to understand the role their security solutions can play at each of these three stages.
Pre-Execution
This is where tools like antivirus, next-gen antivirus (NGAV), and other file-scanning techniques come into play. Once a malware sample has been identified and flagged, these tools can update their blacklists to block it before it can be executed. NGAV tools advance this capability by blocking entire groups of malware that share the similar file attributes as samples that have already been blacklisted.
As the attack against Barts Health shows, however, new malware that has never been seen before can still slip past these defenses undetected. As a result, more comprehensive protection requires additional investment in the next stage before simply giving up and accepting the system needs to be taken offline and restored.
Runtime
The defining characteristic of strong runtime malware defense is the ability to recognize unique behaviors of malicious software before it can do any harm. Assuming that either traditional or next-generation anti-virus solutions are doing their jobs pre-execution, the runtime solution has to be able to catch all of the newest attacks as well as streaming or “fileless” attacks trying to execute on the victim system. This is a very new area, with the new solutions coming to the market at almost the same time as the new attacks which are developed to avoid the earlier protection strategies.
Damage
Good malware detection is still valuable, as there will always be some threat, or some combination of user error and system configuration, that manages to create an opening. When this happens, early detection can be the difference between restoring a backup and filing for a breach notification. Detection comes in many forms, from network and host-based anomaly detection to SIEM analytics to recognizing static indicators of compromise. Once these are seen, early notification and plans for interdiction and clean-up make the damage as limited and short-lived as possible.
Experienced security teams know that every piece of malicious software cannot be caught before it can run, and they know that cleaning up after an event is painful and often incomplete. Runtime malware defense fills that gap, and is the next area of protection investment by both solution providers and their customers.
About Jack Danahy:
Jack Danahy is the co-founder and CTO of runtime malware defense pioneer Barkly, and a 25-year innovator in computer, network, and data security. He was the founder and CEO of two successful security companies: Qiave Technologies (acquired by Watchguard Technologies in 2000) and Ounce Labs (acquired by IBM in 2009). Jack is a frequent writer and speaker on security and security issues, and has received multiple patents in a variety of security technologies. Prior to founding Barkly, Jack was the Director of Advanced Security for IBM, and led the delivery of security services for IBM in North America.
The views, opinions and positions expressed within these guest posts are those of the author alone and do not represent those of Becker’s Hospital Review/Becker’s Healthcare. The accuracy, completeness and validity of any statements made within this article are not guaranteed. We accept no liability for any errors, omissions or representations. The copyright of this content belongs to the author and any liability with regards to infringement of intellectual property rights remains with them.
