In military history, it's called "fighting the last war": addressing yesterday's threats while today's go unrecognized.
Many healthcare organizations are doing exactly that by being blind to the newest threats to the Protected Health Information (PHI).
The environment in PHI risk is changing rapidly. In recent years, most data breaches were the result of lost laptops and other employee miscues. Today, intentional attacks have surpassed inadvertent mistakes as the leading cause of PHI incidents. Criminal hacks against healthcare organizations have increased 125 percent since 2010 – and last year were the leading cause of data breaches for the first time.
Protecting PHI now depends on how well an organization responds to these five critical challenges:
Responding to ever-evolving threats – Many healthcare organizations have already tightened their controls on employee laptop usage, disposal of paper records, and the like. But the greatest threats on the horizon are coming from intruders: automated malware, criminal theft for profit, etc. (see Figure 1 below.)
2015 Ranking of Information Security Threats
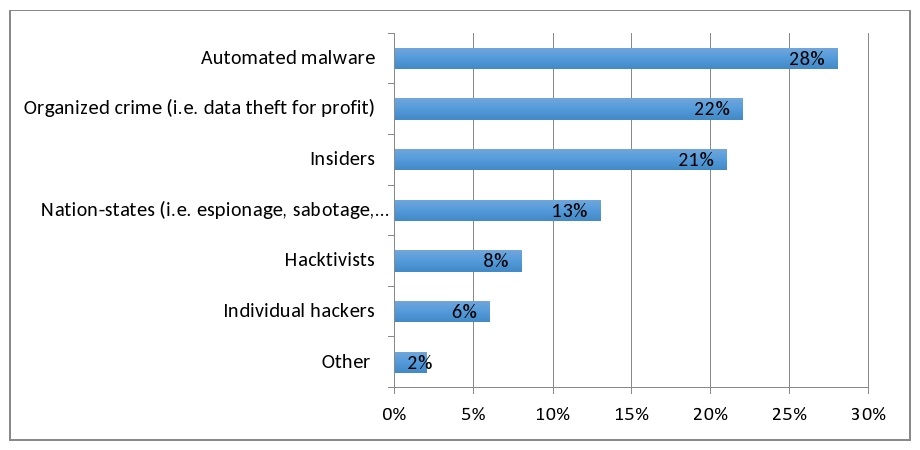
Source: 451 Global Digital Infrastructure Alliance Report, April 2015
It's especially important to not process or store PHI on any hardware/software assets that are no longer vendor-supported (and thus don't receive the latest software patches to protect against new threats). All security-related software in the organization needs to allow for algorithmic updates to protect against mutating malware.
Finding the funding for data security – The growing price tag of the recent Anthem breach ($40 million for notification alone) has opened the eyes of many healthcare leaders. They now know that the average cost of a data breach is nearly $6 million according to the Ponemon Institute.
Many organizations can't find the resources to combat these new threats because of their "technical debt" – the sizeable investment they've already made in Electronic Health Records (EHRs), revenue cycle systems, and so on. But even sufficiently funded organizations often don't know where all their PHI resides.
A structured approach to data security costs less in the long run because an organization first establishes a risk profile and defines the acceptable amount of risk for every process or situation to be protected.
To determine what a breach could potentially cost your organization, just use the free PHI Value Estimator (PHive), created by the American National Standards Institute (ANSI) and others. More dollars become available when management sees that breach clean-up costs a whole lot more than breach prevention.
Organizations should also develop an internal pipeline of security talent. It's less expensive to enhance the security skills of existing staff than to hire pricy pros from other fields who don't have the requisite healthcare experience.
Implementing standards and benchmarks – The gold standard in data security is the National Institute of Standards and Technology (NIST) 800-39 framework because it's a requirement for all federal agencies covered by HIPAA regulations. It's vitally important to benchmark processes for safeguarding PHI, managing HIPAA audits, incident response management, and more. PHive has many features that support this type of rigorous benchmarking.
There are software tools available that use benchmark data to provide a customized view of an organization's risk profile with regard to HIPAA/HITECH requirements. For example, the revised HITECH Act changed how security penalties are levied for an organization's business associates, but didn't really reduce the risk. It's important for covered entities (hospitals, health systems, payers) to include business associates in their risk assessments – and to work collaboratively to improve security processes.
Dealing with organizational inattention to security issues – Despite the many recent headline-grabbing data breaches, many organizations feel that data security isn't a top priority – and is solely an IT issue. But patient privacy and information security need to be organization-wide priorities.
All employees need a periodic update on security policies and procedures – something more substantial than a 10-minute self-guided video. Everyone in the organization should be apprised of each security incident – even the smallest – to offset the "it can't happen here" syndrome. It's even advisable to conduct mock security incidents to see how the organization performs and to adjust benchmarks and goals accordingly.
Finding tools that improve security processes – Far too many healthcare organizations have taken an ad hoc approach to data security, fixing a specific problem after it's arisen. But now there are software tools and services that take a more comprehensive approach to things like risk analysis, incident management, and policy development.
These tools must be able to respond to risks, not just identify them. And while some tools are highly specific (e.g., ensuring compliance with a single regulation), others include detailed dashboards that let organizations monitor a wide variety of security concerns.
We're Under Attack
Data breaches are increasing in both scope and scale. Hacking and malware have now eclipsed the accidental causes of data theft (lost laptops, using an insecure wi-fi connection, etc.). But many organizations are stilled mired in apathy – and many are too invested in EHRs and billing systems to find resources for data security. But to ignore the changing threat landscape is to risk another seven-figure data breach.
Bob Chaput, CISSP, HCISPP, CRISC, CIPP/US, is CEO of Clearwater Compliance in Nashville, Tennessee.
The views, opinions and positions expressed within these guest posts are those of the author alone and do not represent those of Becker's Hospital Review/Becker's Healthcare. The accuracy, completeness and validity of any statements made within this article are not guaranteed. We accept no liability for any errors, omissions or representations. The copyright of this content belongs to the author and any liability with regards to infringement of intellectual property rights remains with them.